Increase in Online-Fraud against Accounting
Certitude has noticed an increase in online fraud against the accounting departments of companies in Germany and Austria in the recent weeks. Attackers make customers change supplier account details via email social engineering. The damage often amounts to several hundred thousand euros and leads to legal disputes between the companies concerned.
These attacks are not new, but what is unusual is the high frequency of such cases over the past few weeks, which Certitude has noticed from companies that are in contact with it. During the analysis, Certitude was also able to determine that scammers systematically collect information on procurement from public tenders in order to gain knowledge about supplier-customer relationships, which is then subsequently used for these attacks.
Involved Parties
For further explanation it is important to understand the following 3 parties involved in this attack:
- Firma-L: A company that provides and invoices services for its customers (supplier)
- Firma-K: A company that receives and pays for services (customer)
- Attacker: Presents itself to the supplier as a customer or to the customer as a supplier
Research and Preparation
The attacks usually begin with the attacker researching Firma-K and the suppliers related to Firma-K. Obtaining this information is usually easier than many would think. For example, the following sources may be useful:
- Press released
- Blog posts
- Corporate social-Media channels
- Announcements from tenders
In the next step, the attacker contacts the two companies by email. The aim of this initial contact is to understand how e-mails from the companies are designed, e.g. in terms of font, signature, writing style. A single e-mail to sales or the company contact address with a general inquiry is usually sufficient and is answered politely most of the time.
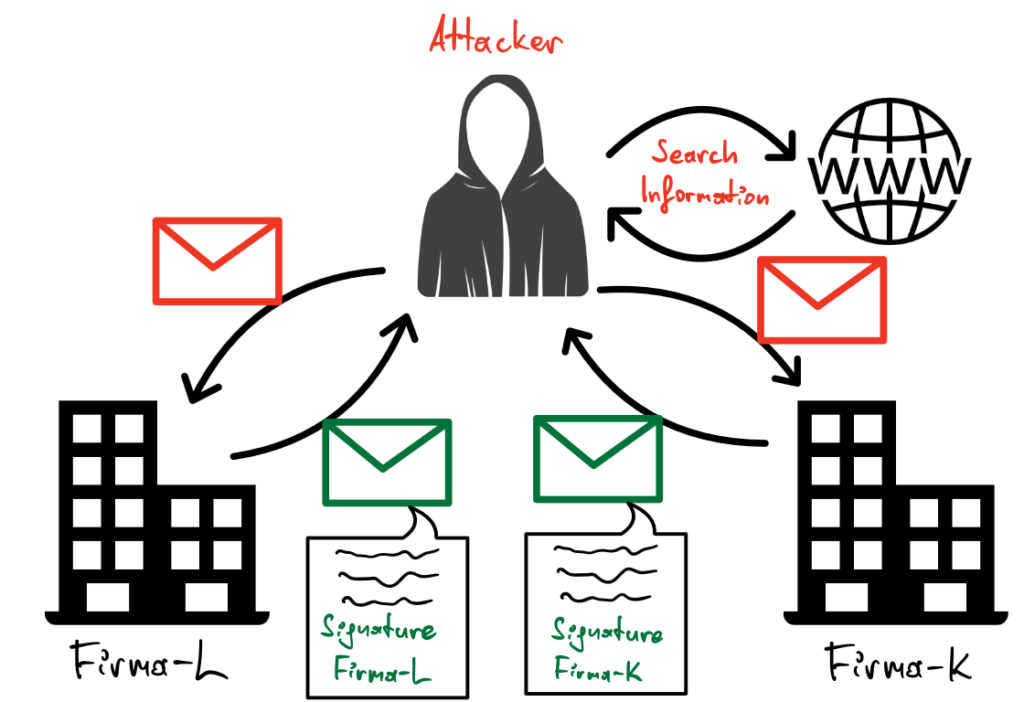
Now the attacker can imitate the e-mails visually and stylistically in order to impersonate the other party in this supplier-customer relationship in future e-mails. The attacker may also register a domain that is similar to the actual company domains or, if no technical measures (such as DMARC, DKIM and SPF) are implemented (unfortunately this is still often the case), he can even send the emails from the original company domains and thus make the attack almost impossible to detect.
Engage in Invoice Communication
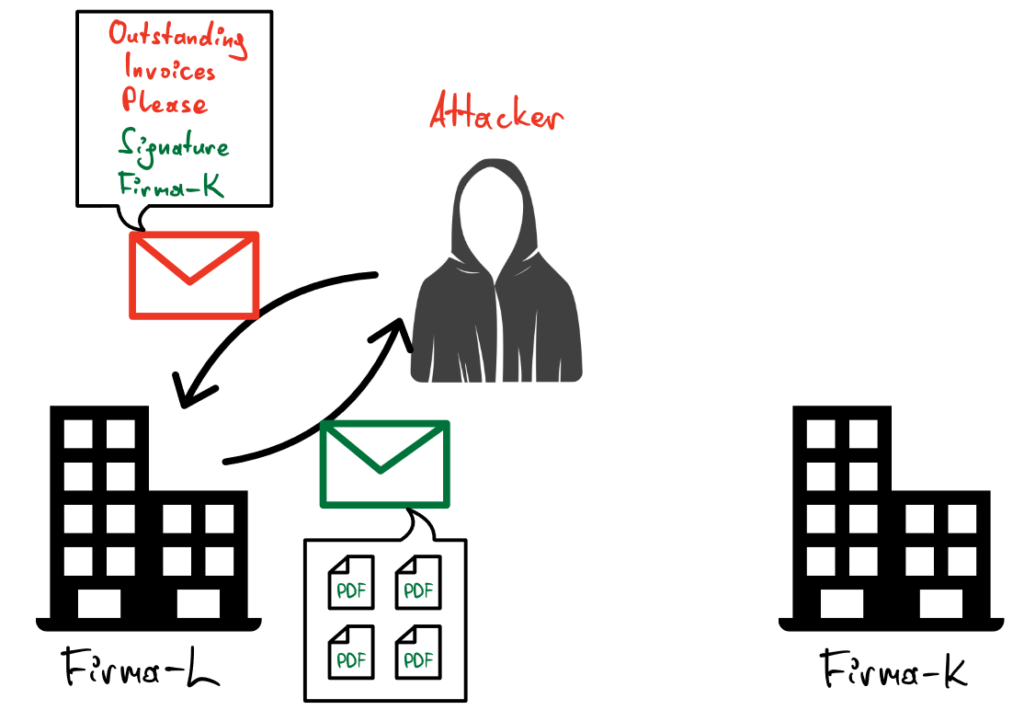
A typical next action would be to contact Firma-L on behalf of Firma-K and ask about outstanding invoices. Firma-L often does not realize that it is the attacker, as the emails are visually and stylistically similar, if not identical, to legitimate Firma-K emails.
The supplier would like to have his outstanding invoices settled and is therefore willing to transmit the outstanding invoice items and documents – without knowing that it is the attacker.
Frequently, email addresses of the attackers remain unnoticed in the communication history (CC field) of future emails regarding invoices in the customer-supplier relationship.
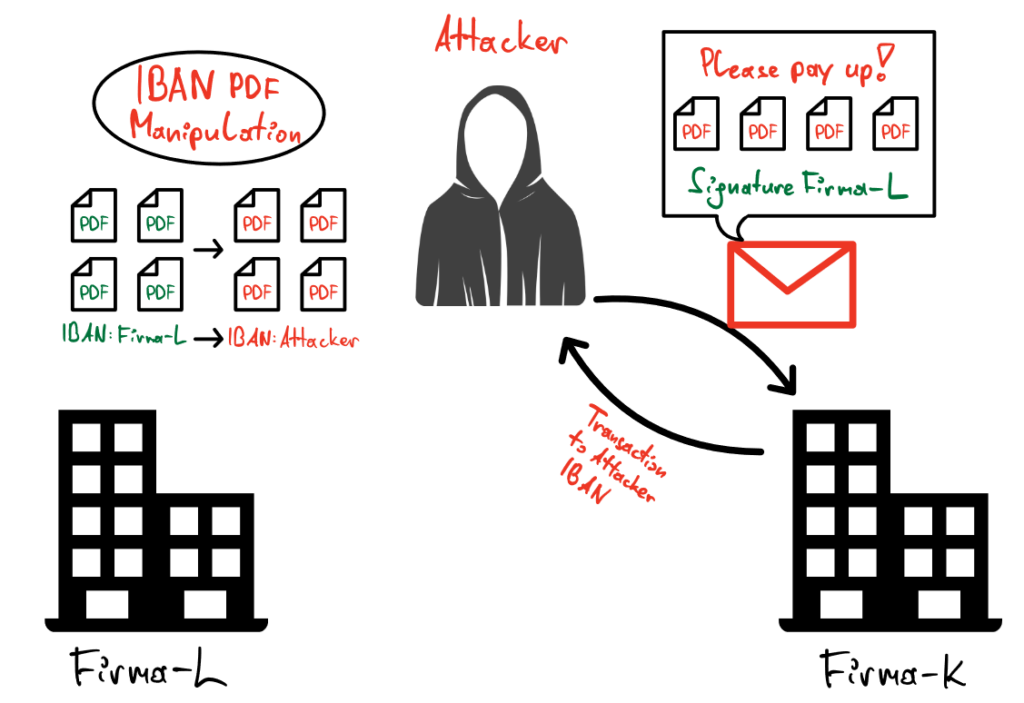
Submission of the Amended Invoice
Now the attacker swaps the account number in the invoice. It is often wrongly assumed that PDF files cannot be modified – this is not the case! The attacker now sends the changed invoice to Firma-K in the name of Firma-L, often with a note about the changed account number in the email body.
The next time Firma-K transfers money to Firma-L, the damage is done. The money is in the attacker’s account (abroad) and is quickly “cashed out”. But at this point in time, Firma-K and Firma-L have usually not noticed anything.
The attack is only noticed after the first query or reminder from Firma-L to Firma-K. This often happens weeks or months after the attack has taken place. Criminal prosecution is difficult because the attacker technically conceals his origin and communicates via countries with which there is no cooperation in law enforcement. The attacker’s bank is also in foreign countries.
Who is the Victim?
Such incidents often lead to legal disputes about the responsibility of the attack between Firma-L and Firma-K, also due to the high amount of damage. Firma-K made the transfer to the wrong account, but Firma-L did not receive its money. Often both of the affected parties made mistakes in the previous communication that made the attack possible.
What Should a Victim Do?
Certitude recommends reporting such incidents quickly and involving experts in the investigation of the incident. The scenario described is just one of various possible attack variants. Forensic analysis of the e-mails can narrow down the attacker’s actions and clarify whether infrastructure was compromised or the attack was based solely on social engineering, according to the scenario described above. The analyzes may allow conclusions to be drawn about the perpetrators.
What should you do preventively?
- Strengthen the security awareness of employees, e.g. through training and self-commissioned phishing campaigns
- Critical review of sender email addresses and domains by staff
- Establish electronic signatures for e-mails and invoice documents between customer and supplier. This makes it easier to spot forged e-mails or documents
- Carry out technical hardening of the e-mail systems in the company, in particular using the technical measures DKIM, DMARC, SPF to prevent e-mail spoofing. Otherwise attackers can even send e-mails in the name of foreign domains