DORA Regulation Update: Introducing the 2nd batch of RTS & ITS

On the 8 of December 2023 the second batch of RTS (Regulatory Technical Standards) & ITS (Implementation Technical Standards) was released. These documents further specify the requirements set out in the Digital Operational Resilience Act (DORA) regulation.
Currently these released documents are in a public consultation phase which will end by 4th of March 2024 and will be finalised until the 17th of July 2024.
| Policy products | Public consultation | Submission to the European Commission |
| First batch of policy products | Completed | 17 Jan 2024 |
| Second batch of policy products | 08 Dec 2023 – 04 Mar 2024 | 17 Jul 2024 |
| Feasibility report on single EU Hub | TBA | 17 Jan 2025 |
In the next sections we will provide information on the essential new aspects and information these documents bring and focus on the areas which potentially have bigger impacts on the affected organisations.
RTS and ITS on major ICT-related incident reporting
Introduction
The draft RTS and ITS on major incident reporting cover three distinct aspects of incident reporting: the time limits for the submission of an initial notification, intermediate and final reports for major incidents, the content of the incident reports for major ICT (information and communication technology) -related incidents, and the content of the voluntary notification for significant cyber threats. By providing clear guidelines for each of these areas, the draft RTS and ITS help ensure that organisations can report incidents in a unified and effective manner.
One feature of the draft ITS is the introduction of a single template covering the initial notification as well as the intermediate and final reports. This template streamlines the reporting process, making it easier for organizations to provide the necessary information in a clear and concise manner.
Timelines
The proposed timelines for reporting major incidents notification and reports are as follows:
- The initial report must be submitted within 4 hours from the moment of classification of the incident as major, but no later than 24 hours from the time of detection of the incident.
- An intermediate report must be submitted within 72 hours from the classification of the incident as major, or when regular activities have been recovered and business is back to normal.
- The final report must be submitted no later than 1 month from the classification of the incident as major.
Incident Notification and Report Contents
In terms of the content of the reports, the draft RTS and ITS provide clear guidelines for what information should be included in each of the three reports. The following details on the contents of each report are areas on which financial entities must focus on when implementing their incident response plans as they need extra reporting efforts which might not arise from internal business needs.
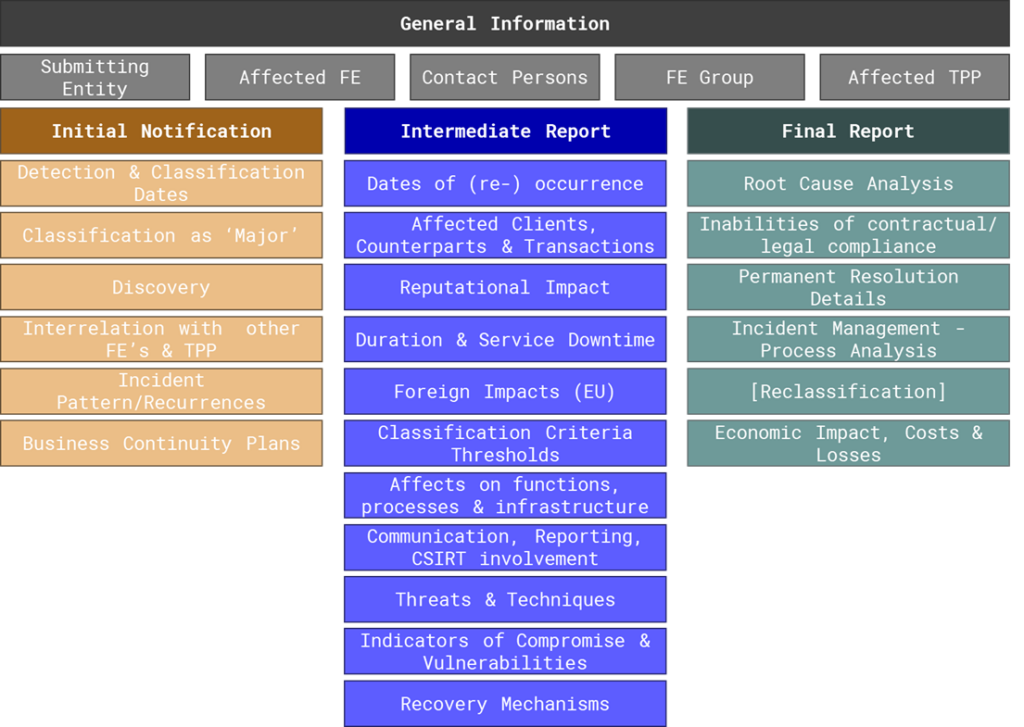
The initial notification must indicate the origin and effect of the incident. Therefore, organisations must be capable to determine early in the incident management process if an incident resulted from or affects other financial institutes or third-party providers.
The initial notification must further include the reoccurrence of incidents. Comparing current incidents to past incidents is an ability that organisation must prepare in their incident management process.
The intermediate report must include the effects on financial counterparties, an analysis that is outside of the organisations own business need. Further the reputational impact of the incident must be analysed and reported. An impact assessment on clients, transactions and financial counterparts must be systematically conducted and reported. A new obligation is that financial entities need to assess the potential impacts on EU Member States by the occurred major incident.
The European Supervisory Authorities further demand a detailed categorization of the incident and the threat actor. Financial institutes must list their affected business processes and business functions, which requires organisations to prepare the interconnectedness of infrastructure components, business functions and business processes. Finally, financial institute must document and report any incident related communication with partners and customers.
The final report must among other things describe any inability to comply with legal and contractual obligations such as SLAs and extensively assess the incident’s financial impact.
RTS on subcontracting of critical or important function
The draft RTS on subcontracting of critical or important functions describes how financial entities must assess the risks associated with subcontracting during the precontractual phase; this includes the due diligence process.
The draft RTS sets out requirements regarding the contractual arrangement regarding the subcontracting conditions for the use of ICT services supporting critical or important functions or material parts thereof ensuring that financial entities can monitor the entire ICT subcontracting chain.
Complexity and risk considerations
The elements of increased or reduced risk shall be considered by financial entities regarding ICT third party service providers and theirsubcontracting services. The most relevant are the due diligence processes of ICT third party service providers and their subcontractors, where the data is processed and stored, the potential impact of disruptions and the concentration risk.
Risk assessment regarding the use of subcontractors
Financial entities must assess their willingness and risk appetite to allow ICT third party service providers to use subcontractors for supporting critical or important functions. By considering several subjects of which the most relevant are, ICT third party service provider need to involve the financial entity in their decision-making process for using subcontractors, assessments of impact of failure and considering obstacles in exercising obligations in contractual agreements.
Description and conditions under which ICT services supporting a critical or important function may be subcontracted
Financial entities must identify which ICT services supporting critical or important functions are eligible for subcontracting and under which conditions. For those eligible, written contractual agreements need to, among other things, contain monitoring & reporting obligations, necessary risk assessments and requirements to follow ICT security standards and usage of security tools.
Monitoring of the entire ICT subcontracting chain by the financial entity
The financial entity must fully monitor the ICT subcontracting chain and must document it. They furthermore need to monitor appropriately subcontracting conditions and use key performance indicators to ensure agreed upon contractual agreements are met.
Material changes to subcontracting arrangements
As mentioned above, financial entities need to be involved in the decision process for subcontracting. ICT third party service providers may implement material changes only after approval or no objection was given until the end of a grace period by the affected financial entity.
Draft Regulatory Technical Standards specifying elements related to threat led penetration tests
In the complex world of financial regulations, staying secure is crucial for both regulators and financial institutions. Digital Operational Resilience Act (DORA) requires certain financial entities to undergo advanced testing every three years using Threat-Led Penetration Testing (TLPT). The now released RTS for TLPT specifies in detail how DORA defines TLPT ‘in accordance with the TIBER-EU framework’.
Key Components of TLPT
- Identification Criteria: The regulatory technical standards specify criteria for identifying financial entities subject to TLPT.
- Testers: The RTS outlines requirements and standards governing the use of internal testers. This includes defining the qualifications, roles, and responsibilities of internal testers involved in the TLPT process. DORA requires that at least every 3rd year external tests are used.
- Scope and Methodology: The RTS provides clear guidance on the scope, testing methodology, and approach for each phase of TLPT. This ensures a comprehensive evaluation, covering all aspects relevant to operational resilience.
- Results, Closure, and Remediation: The RTS addresses the handling of results, closure, and remediation stages. Financial entities are expected to take prompt actions based on the test outcomes, fostering a proactive approach to addressing vulnerabilities.
- Supervisory Cooperation: The directive underscores the importance of supervisory and other relevant cooperation needed for TLPT implementation. This collaborative approach aims to facilitate mutual recognition and harmonize efforts across jurisdictions.
Identification Criteria
Regarding the identification criteria the following overview shows more specifically how TLPT authorities identify financial entities which must undergo TLPT:
- Credit institutions that are considered globally important or other significant institutions according to European regulations.
- Payment institutions and electronic money institutions with a total value of payment transactions exceeding EUR 120 billion in each of the past two financial years.
- Electronic money institutions with outstanding electronic money exceeding EUR 40 billion, in each of the previous two financial years.
- Central securities depositories.
- Central counterparties.
- Trading venues with electronic trading systems meeting specific criteria, including having the highest market share in certain financial instruments at national or EU level.
- Insurance and reinsurance companies meeting specific criteria, including those with Gross Written Premiums (GWP) exceeding EUR 500 million in each of the past two financial years, and those falling within the 90th percentile of GWP distribution for certain activities. Additionally, companies with total assets equal to or higher than 10% of the sum of total assets for the identified activity type in the Member State.
TLPT authorities can however nominate other financial entities according to their impact and systemic character and or ICT risk to be required to perform TLPTs according to the specifications of the RTS document.
Exempt of TLPT
Financial entities mentioned in points above are exempt from conducting Threat-Led Penetration Testing (TLPT) if an assessment based on criteria reveals that their impact, financial stability concerns, or ICT risk profile don’t warrant the test. In cases where multiple entities within the same group share common ICT systems or use the same intra-group service provider and meet the specified criteria, the TLPT authorities in the relevant Member State(s), in consultation with the authority in the state where the group’s parent company is located, may collectively decide whether individual TLPT requirements are necessary for these entities.
We hope that our blog post has provided valuable insights into the second batch release of RTS & ITS under the DORA regulation. If you or your organization are seeking expertise, Certitude is ready to assist you by offering knowledge on DORA and its associated RTS & ITS. Feel free to reach out for support.