How malware infects the company over private devices
Security situation worsened by home office
In the past year, many organizations were suddenly faced with the challenge of providing employees with a home office workstation within a very short time. While these measures protected the health of the employees, they could potentially endanger the IT security of their employers.
It is now common practice in many organizations to allow employees to access company resources from their private computers. This is done in order to provide employees with a workplace as quickly and easily as possible. But private systems are heterogeneous and are not managed centrally by a professional IT team. As a result, they offer more opportunities for attack and open loopholes for criminal intruders.
In such cases, companies with consistent IT security use a remote desktop solution (e.g. Citrix or RDP), via which employees get “the screen” of their work PCs and can thus access their usual work environment. In order to ensure a separation between private and professional IT environment, certain functions of the remote desktop solutions are deactivated. Employees should not be able to copy data between their private and professional environment, print from the professional environment on private printers or transfer data from USB sticks connected to their private computers to the company environment.
After installing these restrictions, many companies and their IT managers assume that infected private computers pose no threat to the company. However, this assumption is incorrect because malware running on private hardware can interact with the remote desktop just like the legitimate user. For example, a malicious program can simulate keyboard and mouse inputs in order to import malware into the company’s IT.
Demonstration of the attack
The cyber security experts from Certitude, who have already uncovered weaknesses in Microsoft and Citrix products, demonstrate the following scenario in a simulated hacker attack (click here for the video): A victim is infected with malware via a fake YouTube download. This is not noticeable. The attacker can already transfer the victim’s screen content to himself and read sensitive data. The victim then accesses the company computer via remote desktop. The malicious program running in the background interacts unnoticed with the company’s remote desktop via simulated keystrokes, transfers malware to the company computer and executes it. The malware activates a crypto Trojan horse (“ransomware”), encrypts the company data and thus blackmails the victim for ransom payments.
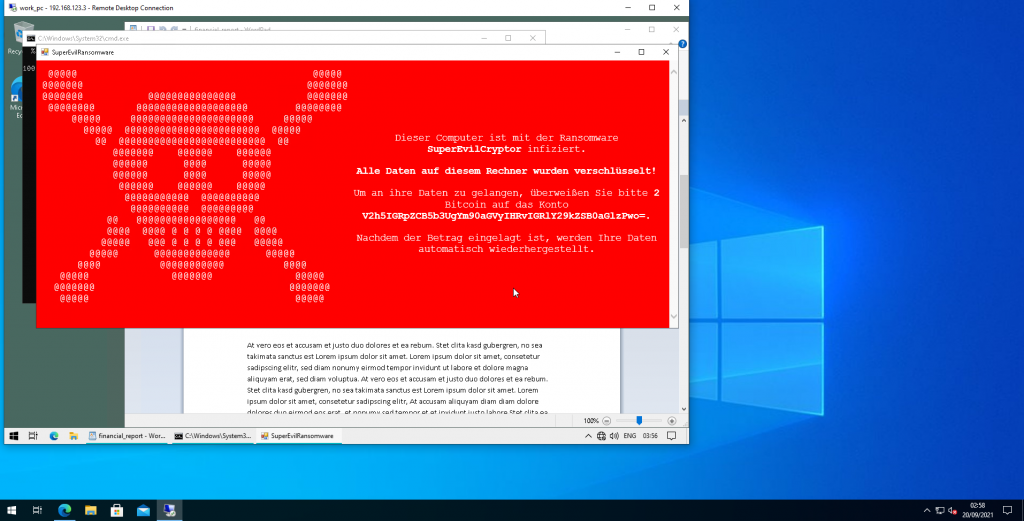
This attack shows that when private devices access corporate networks, implicit trust is placed in the security of private devices that are not within the organizational sphere of influence. It cannot be guaranteed that private systems are securely configured and free of malware, that the installed software is up-to-date and that the systems are only used by employees and not their friends or relatives.
Countermeasures
For many companies with strict security requirements, it is advisable to equip employees for their business activities with company devices that are centrally administered and monitored and not to allow the use of private devices. Without this measure, protection is very much dependent on the individual employees, their private devices and their know-how about the safe use of IT. In this case, employees should definitely be trained and sensitized so that they are able to operate their private hardware with an appropriate level of security.
Examples of safe use of a personal device include:
- Keep operating systems and software up-to-date – regular updates and virus protection
- Do not install dubious or unknown programs
- Physical protection from other people (screen lock, hard disk encryption)
- Use strong passwords
- Exercise extreme caution when clicking on links or attachments