Thousands of Organizations Vulnerable to Subdomain Hijacking
Subdomain Hijacking presents a concerning scenario where attackers take control of websites hosted on subdomains owned by reputable organizations, enabling them to carry out activities such as malware distribution, disinformation campaigns, and phishing attacks. The surge in cloud service adoption coupled with the proliferation of disinformation and phishing efforts has intensified the magnitude of this vulnerability.
Certitude Consulting has detected instances of subdomain hijacking attacks targeting prominent public authorities. While this vulnerability is not novel, we have undertaken a comprehensive analysis to gauge its gravity, yielding alarming outcomes. Through an examination of a limited sample of cloud services and DNS records, we identified over 1,000 susceptible organizations. Among these are notable entities like the Australian Department of Foreign Affairs and Trade, CNN, Stanford University, and FPÖ. However, we assume that the scope of affected domains could encompass several hundred thousand or more.
The implications of a subdomain takeover are far-reaching, encompassing a spectrum of potential attacks:
Malware Distribution: Attackers can employ the subdomain as a hosting platform for distributing malicious software.
Disinformation Spread: Malicious actors capitalize on the credibility of reputable entities such as media outlets, government bodies, or universities, using subdomains to disseminate false information. This undermines public trust in reliable sources, fosters disinformation campaigns that manipulate public opinion, and destabilizes communities and societies.
Phishing Attacks: Attackers can craft convincing phishing pages using the subdomain to trick unsuspecting users into revealing sensitive information.
Social Engineering Attacks: The subdomain can serve as a launching pad for compelling social engineering campaigns, manipulating individuals into disclosing confidential data or engaging in harmful activities.
To forestall potential attacks and raise public awareness about this widespread vulnerability, we have proactively assumed control over websites belonging to particularly susceptible organizations and informed them.
Government, Party, University and Media Websites Affected
We have taken over blogs hosted on WordPress.com for the Australian Department of Foreign Affairs and Trade (https://blog.dfat.gov.au), the UK Meteorological Office (https://blog.theukmetoffice.gov.uk), the US states of Rhode Island (https://blog.health.ri.gov) and Nebraska (https://test.ne.gov) as well as US Based Varobank (https://blog.varobank.com).
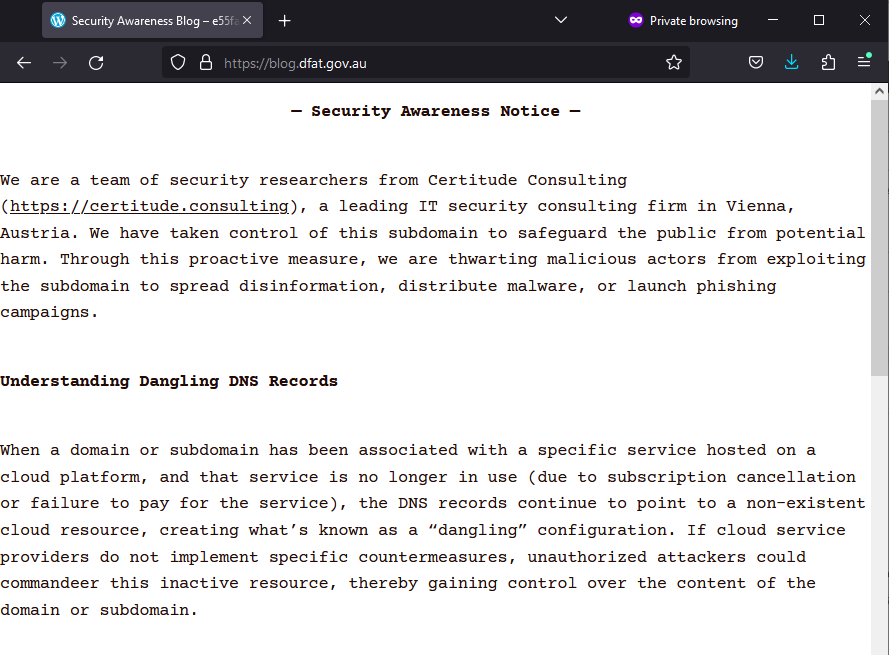
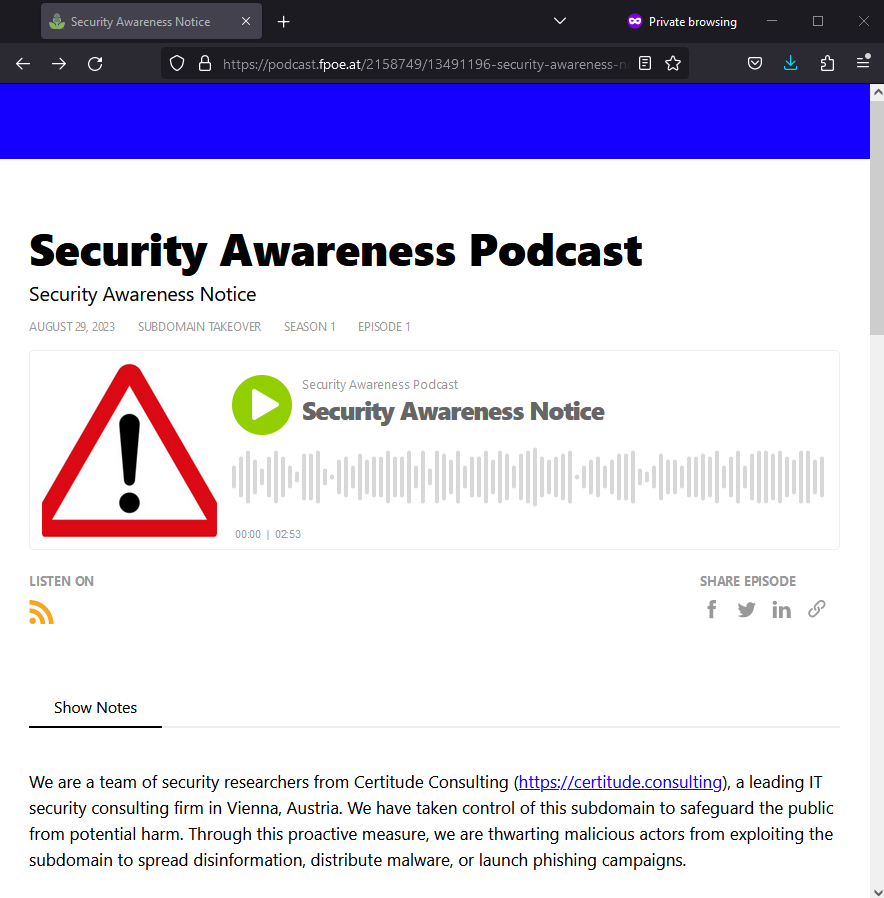
Additionally, AWS S3 Buckets referenced by DNS entries from German Ergo Group’s insurance subsidiary Nexible (http://s3.nexible.de/index.html) and Germany-based tobacco conglomerate Dannemann (http://img.dannemann.com/index.html) have been secured by Certitude Consulting. Furthermore, the podcast platforms hosted by Buzzsprout for the Austrian political party FPÖ (https://podcast.fpoe.at), Nasdaq-listed technology firm Netscout Systems (https://podcast.netscout.com) and US insurance giant Penn Mutual (https://podcast.pennmutual.com/) have been taken over. The situation becomes even more concerning as valid TLS certificates were issued for websites hosted on platforms like WordPress or Buzzsprout. This aspect further magnifies the illusion of content legitimacy, making the potential threats even harder to discern.
A similar approach enabled the forced redirection of subdomains. However, no valid TLS certificate is issued in this case. In this manner, we took control of websites belonging to news network CNN (http://insession.blogs.fortune.cnn.com), the government of the Canadian province Newfoundland and Labrador (http://atippblog.gov.nl.ca), international non-governmental organization Caritas (http://blog.caritas.org), US-based Bankfive (http://blog.bankfive.com), University of California (http://blog.admission.ucla.edu), University of Pennsylvania (http://blog.wic.library.upenn.edu) as well as Stanford University (http://shaqfehgroup.stanford.edu) and redirected them to a newly created WordPress blog (http://subdomainhijackingblog.wordpress.com).
Understanding Subdomain Hijacking
The Domain Name System (DNS) operates as a hierarchical and distributed naming system for online resources such as servers and services. When an organization opts for a cloud service, it creates an account within the service, incorporates resources and materials, and subsequently associates the cloud service with its DNS records on its own DNS servers:
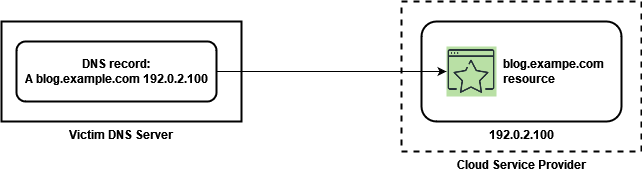
When a domain or subdomain has been associated with a specific service hosted on a cloud platform, and that service is no longer in use (due to subscription cancellation or failure to pay for the service), the DNS records continue to point to a non-existent cloud resource, creating what’s known as a “dangling” DNS record:
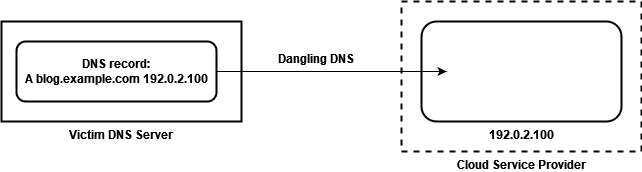
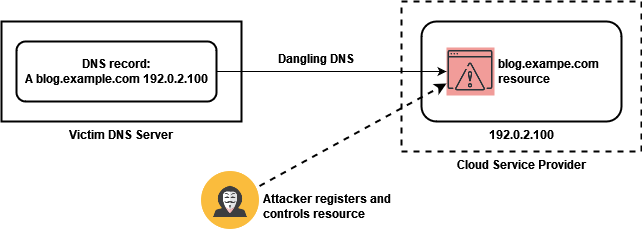
If cloud service providers do not implement specific countermeasures, unauthorized attackers could register an account on the cloud platform and link it to the dangling DNS records. As the organization’s DNS records still point to the endpoint of the cloud platform, the attacker effectively seizes control over the subdomain, a scenario referred to as “subdomain hijacking” or “subdomain takeover”:
Preventing Subdomain Hijacking
Certitude Consulting recommends that all organizations to regularly audit DNS records and to deactivate cloud resources only after associated DNS records have been removed.
In most cases, the hijacking of subdomains could be effectively prevented by cloud services through domain ownership verification and not immediately releasing previously used identifiers for registration. Therefore, Certitude Consulting also urges cloud service providers to implement such protection mechanisms. Microsoft implemented this for Azure Storage Accounts several months ago. Other providers, such as Amazon Web Services, have not yet implemented such mechanisms.
Research Methods and Disclosure
Enumeration methods for dangling DNS records or any vulnerability details identified during this research will not be disclosed publicly at this time. All organizations mentioned in this post have been contacted because of their dangling DNS records. It was not feasible to inform all >1.000 organizations. Coordination with the Austrian CERT is in progress.
References
Archived URLs:
https://web.archive.org/web/20230829125434/https://blog.dfat.gov.au/
https://web.archive.org/web/20230830055441/https://blog.theukmetoffice.gov.uk/
https://web.archive.org/web/20230830055450/https://blog.health.ri.gov/
https://web.archive.org/web/20230830055510/https://test.ne.gov/
https://web.archive.org/web/20230830055605/https://blog.varobank.com/
https://web.archive.org/web/20230830055650/https://podcast.fpoe.at/2158749/13491196-security-awareness-notice
https://web.archive.org/web/20230830055750/https://podcast.netscout.com/2235256/13491204-security-awareness-notice
https://web.archive.org/web/20230830060251/https://podcast.pennmutual.com/2235346/13491211-security-awareness-notice
https://web.archive.org/web/20230830055940/http://s3.nexible.de/index.html
https://web.archive.org/web/20230830060404/http://img.dannemann.com/index.html
https://archive.is/RIVVu
https://archive.is/AqTBG
https://archive.is/f0SfN
https://archive.is/6kb5c
https://archive.is/poPl2
https://archive.is/ZLuWG
https://archive.is/YIPVZ