ISMS for industry based on IEC 62443

Requirements from NIS2 (critical infrastructures) for manufacturing companies and operators of essential services as well as specific requirements for information security for specific sectors (e.g. automotive) increasingly refer to the IEC 62443 standards framework.
Requirements from NIS2 (critical infrastructures) for manufacturing companies and operators of essential and important services as well as standard-specific requirements for information security in specific sectors (e.g. automotive) increasingly refer to international standards, with the IEC 62443 framework of norms having been established as the standard for Operating Technology (OT).
The operators, system integrators, maintenance companies and component manufacturers in this segment see themselves increasingly challenged to protect their industrial automation systems or their production from potential cyber attacks and to bring about and clearly document an improvement in the integrity and availability of the components and systems.
The framework of IEC 62443 provides essential assistance and an internationally aligned orientation for all 4 target groups. IEC 62443-2-1 defines as a central standard element the implementation of an information security management system for the operator (asset owner) of industrial automation and control systems (IACS). Important topics (so-called Security Program Elements (SPE)) include:
- Organizational responsibilities and policies of the organization as well as
- security checks and risk management but also
- Configuration management as well
- Network and communications security
to name a few.
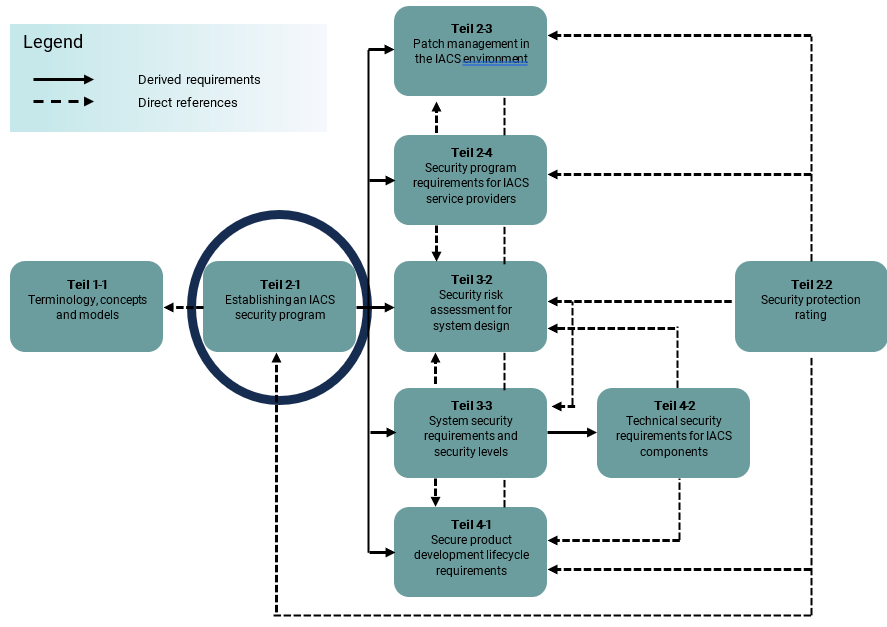
A very important part is the requirement specification of the operator’s IT security program for the service providers for industrial automation systems and vice versa. Further standard parts for this are IEC 62443-2-4 (requirements for the IT security program of service providers) and IEC 62443-3-2 (security risk assessment and system design). The technical safety requirements for components and their life cycle for safe product development are discussed, for example, in parts 4-1 and 4-2.
The collaboration between the key roles of operators/integrators/maintenance companies and component manufacturers contributes significantly to the safe operation, availability of systems and thus the avoidance of financial damage.
The graphic below shows the dependencies and interaction of the individual standards in the IEC 62443 framework.
Certitude advises operators in the field of industrial automation technology and control systems as well as component manufacturers, who want to base their activities on the IEC 62443 framework or are required to do so.
Our services include:
- Building the information security management system in the OT area
- Gap analyzes to determine the minimum requirements that still need to be implemented
- Support in assessing the degree of implementation through measures taken
- Design, adaptation and, if necessary, implementation of a framework for an ISMS including risk management, guidelines, processes and guidelines
- Support in implementing the required measures in the company
- Targeted treatment of subject areas from the guideline as well as the recommended type of implementation for the client
- Support in the selection and implementation of technical measures to defend against cyber attacks
- Penetration testing of OT networks or systems to identify exploitable vulnerabilities for operators
- Security checks of products (hardware, firmware, software) for manufacturers
The type of collaboration is coordinated between the client and Certitude as part of project preparation and execution and can therefore be regularly adapted to requirements.
The client’s cooperation is required at least to provide the necessary information and to make essential decisions. The extent of the client’s necessary cooperation depends on the type of support service chosen by the client.
Should your organization seek guidance in securing OT products or OT infrastructure according to best-practices, our team is ready to assist. For more information contact us directly.