Ransomware Actor May Have Leaked Their Previous Victims
Recently we were tasked with investigating a ransomware attack case. We were able to reconstruct the likely attack vector and identify the data that was likely stolen. What made this case particularly interesting was the mechanism used to exfiltrate data, as it may have revealed other organizations previously attacked by this group.
After being called to the case, the initial assessment of the situation revealed that, luckily, some of the organization’s offsite backups were not encrypted. This data gave us the opportunity to review logs and other data that was present before it was encrypted.
Attack Vector
Through an analysis of the external infrastructure, a critical (known) vulnerability (CVE-2018-13379) [1] was identified in the Fortinet firewall (FortiOS SSL VPN). This directory traversal vulnerability allows an unauthenticated attacker to access system files through specially crafted HTTP requests. The vulnerability can easily be exploited to disclose active VPN usernames and their associated passwords.
The following URL was accessed to verify the vulnerability:
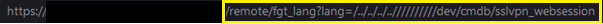
VPN usernames and corresponding passwords were contained in the downloaded file:

The vulnerability became known at the end of May 2019. Over the time threat actors leaked VPN access information (links and web sessions) in different forums.
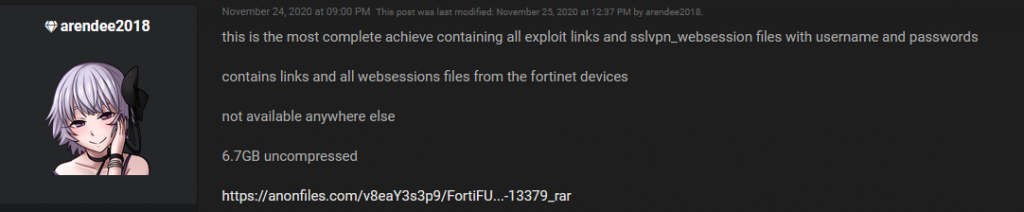
The last leak was in September 2021 where SSL-VPN access information to 87,000 FortiGate SSL-VPN devices got published [2]. This information was probably used by different threat actors to infiltrate companies, exfiltrate data and deploy ransomware.
After further analysis it turned out that an exposed VPN user (Domain Admin) was used to establish a VPN connection and infiltrate the customer. This was possible because at this time no second factor (2FA) was required for a VPN login. Log data revealed that a device with the name “mimikatz” (like the well-known tool for credential dumping) was used to access the infrastructure.
Data Exfiltration
The attacker installed the Dropbox client on the Domain Controller (DC) to exfiltrate data from a network share. The exfiltrated archive was not deleted and could be recovered from a backup of the not-yet encrypted DC. Therefore it was possible to identify the affected data.
The attacker unintentionally disclosed the content of the used Dropbox account, which contained folders with names of other companies. This suggests that data from those companies was stolen as well (of course another possibility is, that the attacker was trolling us by intentionally leaving fake clues). However, the content of this folders could not be accessed, because the data was not configured to be synchronized on the system.
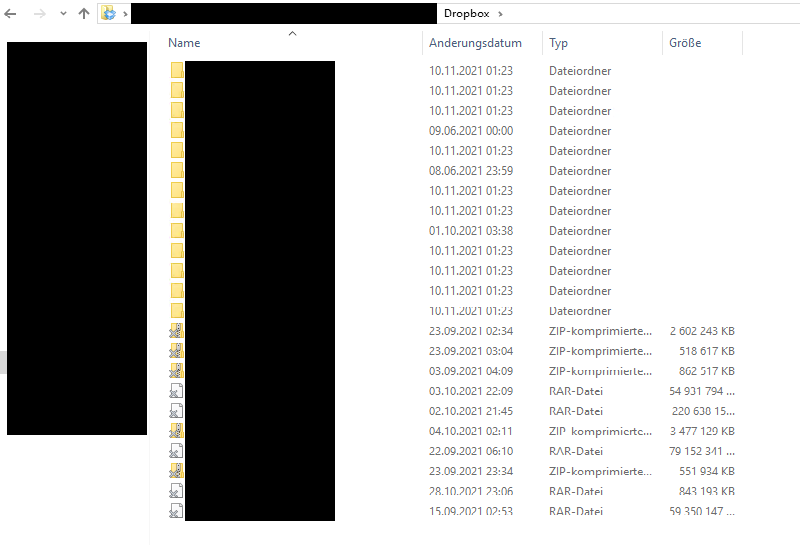
This information was shared with CERT AT.
Encryption
After exfiltrating the data, the process of encrypting several server systems was started. The deployed ransomware is known as “Makop”. Following ransomware note was found on compromised and encrypted systems:
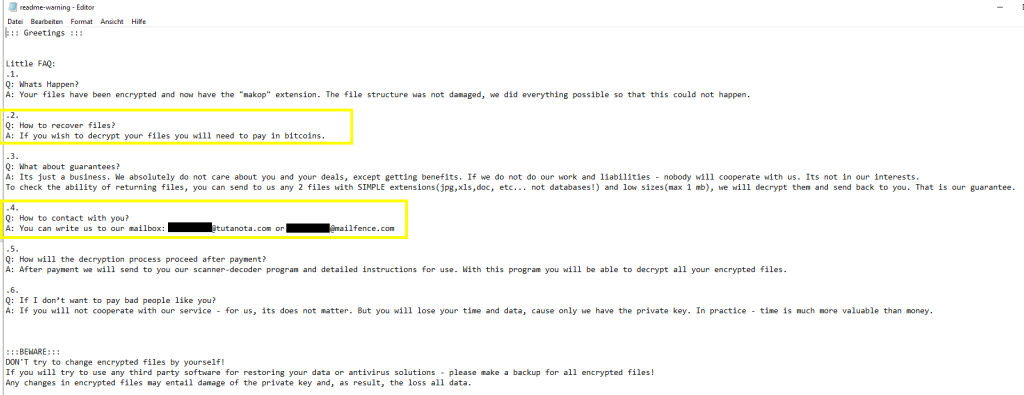
A detailed analysis of the ransomware malware was not performed during this investigation.
Conclusion
As this case, again, shows, it is of critical importance to update all software components as soon as security patches are available. A holistic patch management process, that encompasses operating systems, applications, software libraries, network appliances and any other asset that utilizes software should be established. As they are the primary interface exposed to the world, internet-facing applications are of particular importance. Another takeaway is that multifactor authentication for internet-facing applications is essential not only to prevent classic phishing attacks.